Cybersecurity companies face a unique challenge in B2B marketing.
Buyers are cautious. They don’t rush decisions. They research extensively, validate information internally, and involve multiple stakeholders before speaking with vendors. Because of this, traditional inbound marketing and paid ads often struggle to deliver consistent, high-quality leads.
This is where content syndication for cybersecurity companies becomes powerful.
Content syndication helps cybersecurity marketers place valuable, educational content in front of the right audience at the right stage – while buyers are still researching.
In this blog, you’ll learn:
- why content syndication works so well for cybersecurity
- how it supports high-quality B2B lead generation
- how intent data strengthens results
- what strategies and KPIs matter most
Why Cybersecurity Companies Need Content Syndication
Cybersecurity buyers are research-driven
Security buyers don’t respond well to aggressive sales messaging. Instead, they spend most of their buying journey researching independently, reading reports, comparing frameworks, and discussing internally.
By the time they speak to a vendor, they already have strong opinions.
The cybersecurity market is crowded
Whether your solution focuses on cloud security, IAM, Zero Trust, XDR, or GRC, buyers see similar messaging everywhere. Relying only on SEO or paid ads often means you reach them too late.
Content syndication fills the early-visibility gap
Content syndication places your content inside trusted third-party platforms where cybersecurity professionals already consume information. This allows you to influence buyers earlier – before vendor shortlists are formed.
What Is Content Syndication for Cybersecurity?
Content syndication for cybersecurity companies is the strategic distribution of gated, high-value security content through third-party publishers, industry platforms, and professional networks.
When buyers access your content, they voluntarily share professional information such as:
- job role
- company name
- industry
- region
This creates permission-based B2B leads aligned to specific security topics.
How cybersecurity content syndication is different
Unlike generic content distribution, cybersecurity syndication is:
- tightly targeted by role and industry
- aligned with real security initiatives
- measurable by asset-level performance
Content types that work best
Cybersecurity buyers engage most with content that supports decision-making:
- threat landscape reports
- Zero Trust and identity frameworks
- security maturity benchmarks
- buyer’s guides and evaluation checklists
- risk-focused case studies
How Content Syndication Supports Cybersecurity Lead Generation
Successful cybersecurity content syndication programs follow a clear process.
Cybersecurity content syndication follows a structured process that connects early research signals to pipeline outcomes.
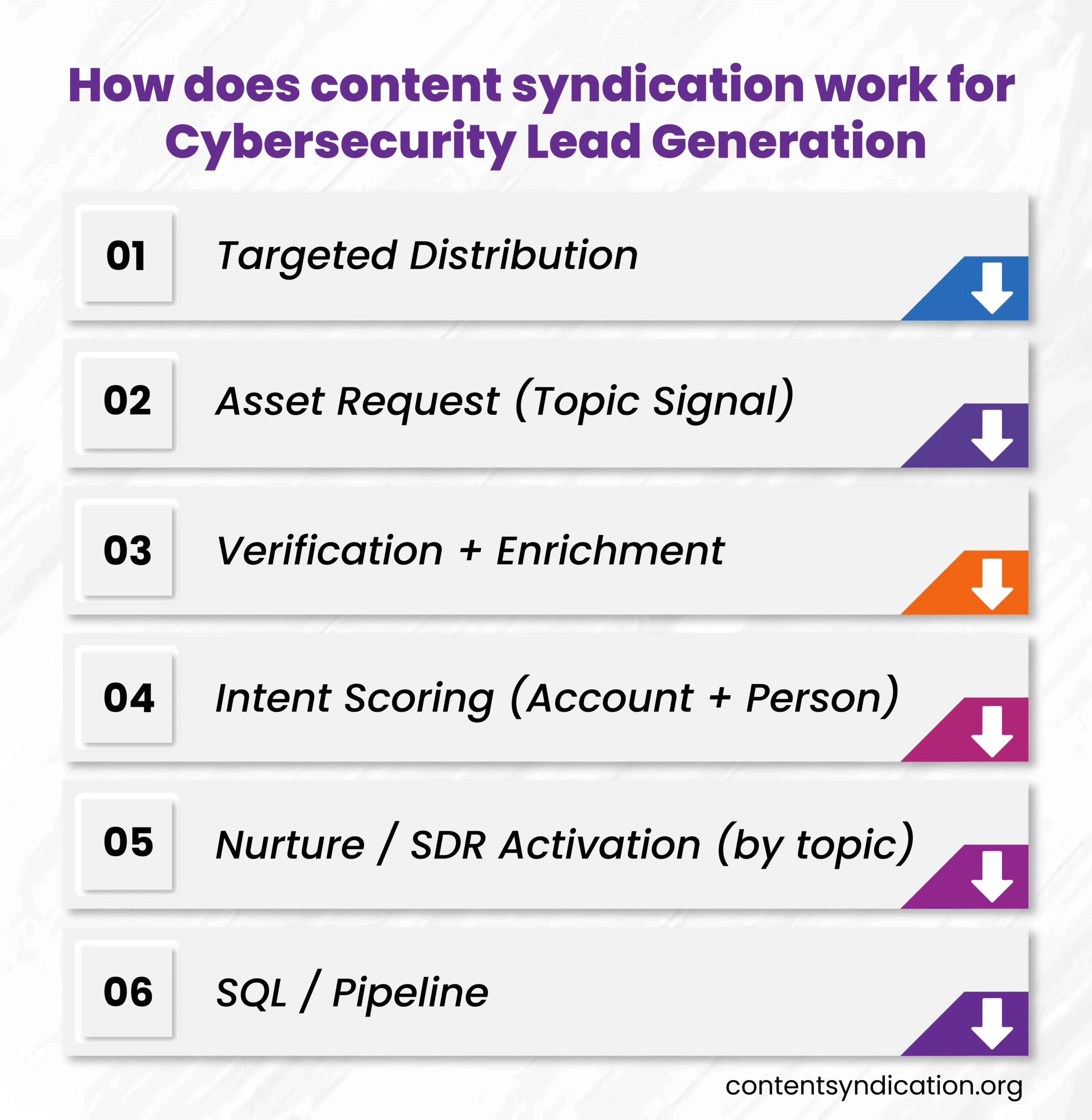
Each of these steps helps cybersecurity marketers move from early research signals to sales-qualified opportunities.
Step 1 – Focus on a specific security problem
Broad messaging rarely works. Instead, high-performing campaigns focus on clear use cases such as:
- ransomware preparedness
- identity governance
- cloud posture risk
- audit and compliance readiness
Step 2 – Promote genuinely useful content
The best assets help buyers:
- understand risk
- assess maturity
- compare approaches
- plan next steps
Product-heavy assets usually underperform.
Step 3 – Distribute through cybersecurity-focused channels
Syndicating content through platforms trusted by security professionals ensures relevance and higher engagement.
Step 4 – Capture topic-specific demand signals
Instead of just collecting contacts, marketers gain insight into:
- who engaged
- which topic drove interest
- how well the lead matches the ICP
This enables smarter follow-up and nurturing.
The Role of Intent Data in Cybersecurity Content Syndication
Content syndication shows what buyers engage with.
Intent data shows how active their interest really is.
Why intent data matters in cybersecurity
Cybersecurity buying cycles are long and non-linear. Buyers may research for months before engaging sales.
Intent data helps teams:
- identify accounts actively researching security topics
- prioritize outreach based on readiness
- avoid premature sales contact
When used correctly, intent data turns syndication into a pipeline acceleration tool.
Best Practices for Cybersecurity Content Syndication
Different cybersecurity content assets work best for different buyer roles. This framework shows how to align assets, personas, and CTAs for better syndication performance.
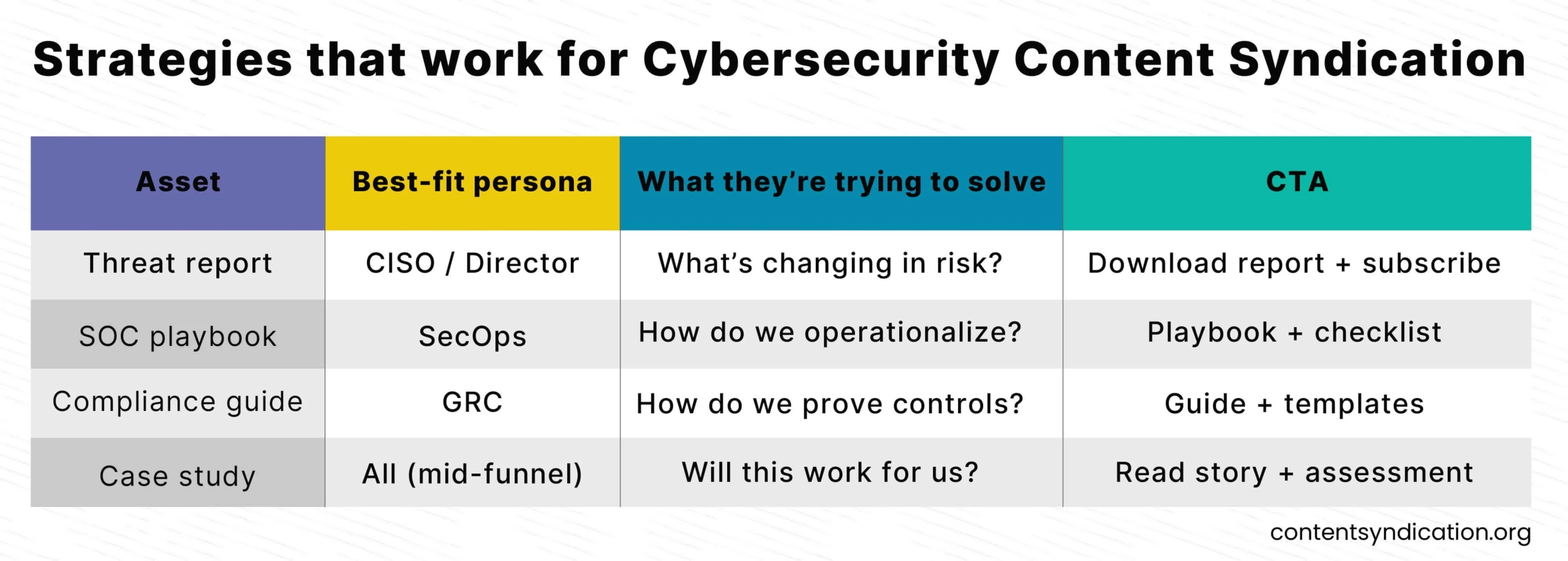
How different cybersecurity content assets align with buyer roles, problems, and CTAs in content syndication campaigns.
Lead with the security problem, not the product
Risk-focused content consistently outperforms feature-driven messaging.
Design content for the buying group
Cybersecurity decisions involve multiple roles:
- CISO and security leadership
- SecOps teams
- GRC professionals
- Cloud and IT teams
Aligning content to each role improves relevance.
Gate for quality, not friction
Ask only for information needed to qualify leads. Too many form fields reduce engagement without improving lead quality.
Balance automation and SDR outreach
Use automated nurture for early-stage interest and SDR outreach only for high-fit, high-intent accounts.
Let intent guide activation
Outreach should match buyer readiness, not internal pressure.
KPIs That Matter in Cybersecurity Demand Generation
Measuring success requires more than just CPL.
Metrics high-performing teams track
- ICP match rate
- inquiry-to-MQL and MQL-to-SQL conversion
- speed-to-lead for high-intent accounts
- pipeline influence
- multi-asset engagement trends
In cybersecurity, quality always matters more than volume.
Common Mistakes That Reduce Lead Quality
Targeting generic IT audiences
Cybersecurity buyers are not the same as general IT audiences.
Over-gating content
Excessive form fields hurt conversion rates.
Premature sales outreach
Contacting buyers too early damages trust.
Measuring success only by CPL
Low CPL without ICP alignment creates noise.
Final Thoughts
Content syndication aligns naturally with how cybersecurity buyers learn and make decisions.
It builds early credibility, supports long research cycles, and surfaces intent without forcing premature sales conversations. When executed with strong content, precise targeting, and intent-driven follow-up, content syndication becomes a reliable engine for cybersecurity demand generation.
Frequently Asked Questions (FAQs)
Is content syndication effective for cybersecurity startups?
Yes, especially when focused on a specific security problem and defined ICP.
What content works best for CISOs?
Benchmarks, maturity frameworks, and risk-focused guides.
How many form fields should we use?
Enough to qualify leads without creating friction.
How do we avoid low-quality leads?
Tight targeting, validation, and intent-based activation.
Is intent data mandatory?
Not mandatory, but highly valuable for long buying cycles.




